
No one enjoys change. Wrapping our minds around protecting our organizations is hard enough for those that do it full time. Communication of the issues and challenges you face to better secure the organization is paramount.
CISA has established Cybersecurity Performance Goals (CPGs) and organized them to align with the NIST CyberSecurity Framework (CSF) functions. A result of this is the CISA CPG Checklist. An easy to read and use checklist to start to create a baseline understanding of where your program is sufficient as well as where there are gaps. This vendor agnostic checklist can help you create the story to tell.
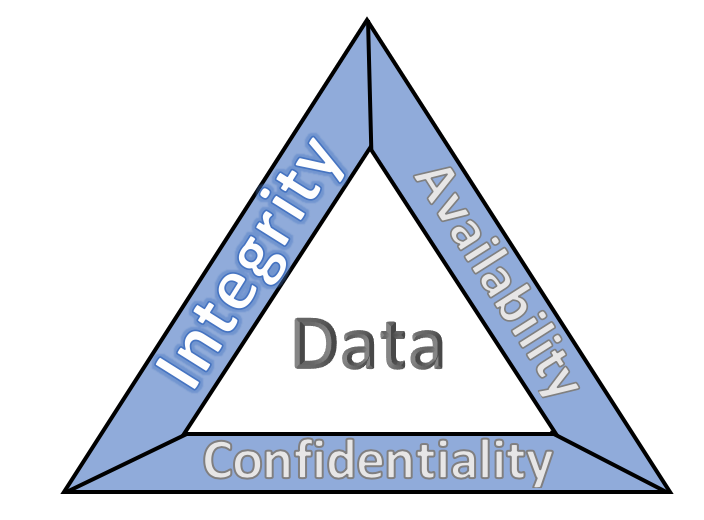
A key first step is focusing on shared objectives. An Information Security program that shares and supports business objectives guided by the CIA Triad of confidentiality, integrity and availability, ensures that the data the business relies on is as those words imply – protected from unauthorized access, authentic and accessible.
Maintain the positivity of the message. Improving your program will be hard work and sometimes requires additional budget spend. The goal is the return on investment by protecting the digital assets of the company.
Address the business needs during these conversations. All functions of the organization need to work together.
Tell a story. Persuade others so that they understand and value these shared objectives.
An natural extension of communicating the Information Security goals and objectives of your organization is to set those expectations with your vendors and suppliers. In the next article, we will discuss Third Party Risk Management and the crucial role it plays in protecting your data as well as understanding how the third party is ensuring critical uptime and business continuity by protecting the organization through Information Security controls. Onboarding a new vendor is a long process. Confirming they have similar objectives can ensure they will be a long term partner.





